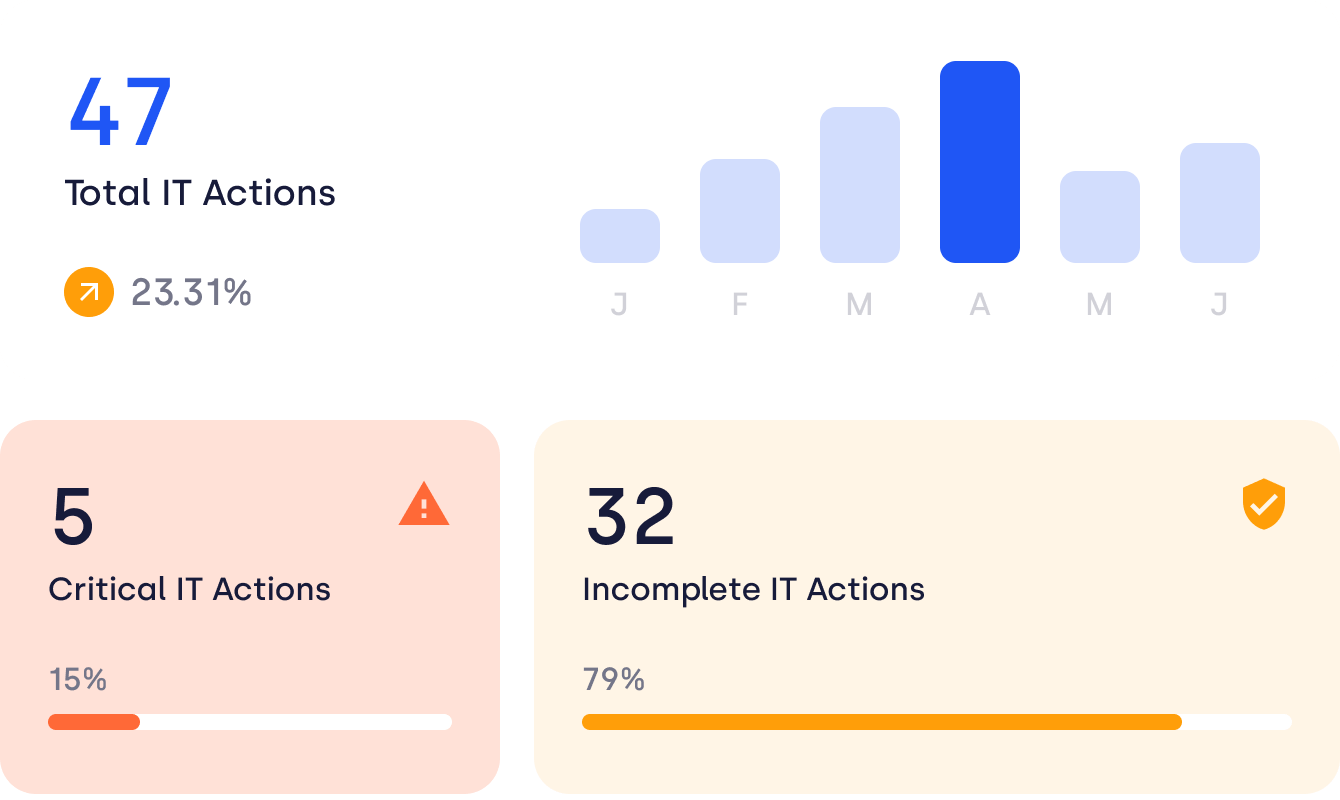
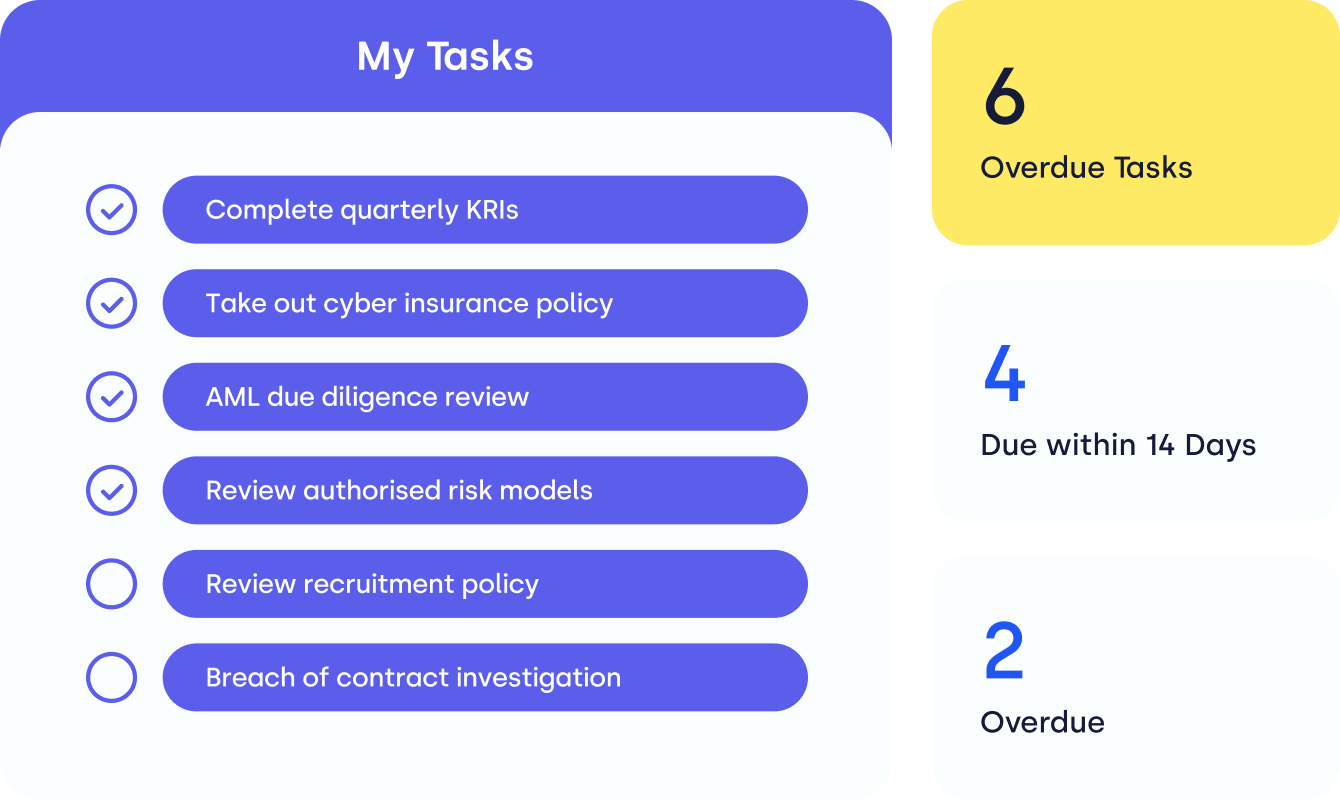
Single source of truth
Create a single source of truth for IT risk management. Get organised for any required action with powerful linking of real-time data.
-
Centralise libraries and registers for IT risk, controls, activities and policies
-
Set up calendars for testing and reviews
-
Dynamically link risks, controls and other data sets
Assess and monitor
Gain a clear picture of your IT security risks and quickly identify critical vulnerabilities from asset risks to incidents.
-
Analyse assets and asset risks
-
Manage IT risk controls and assurance
-
Monitor IT security activities and incidents
Streamline your IT controls
Efficiently ensure compliance with IT Risk frameworks such as NIST, ISO 27000 and PCI DSS.
-
Manage compliance with multiple ISMS control frameworks
-
Demonstrate applicability of controls
-
Map your master control framework to track compliance with other frameworks
-
Create consistency in management with centralised libraries of risks and controls
Manage regulatory change
Integrate compliance content from LexisNexis to stay on top of current obligations and prepare for regulatory changes in cybersecurity.
-
Connect to a LexisNexis feed for your particular industry and location
-
Be alerted to upcoming changes
-
Ensure understanding with regulatory advice in plain English
Act and communicate
Ensure rapid, accurate responses and seamless communications through user-centric interfaces and powerful visualisations and reports.
-
Engage staff through user-centric dashboards
-
Optimise productivity with automated workflow alerts and reminders
-
Create custom PDF, Excel and PPT reports
-
Present clear visualisations and consolidated reports at the click of a button
Information security brochure.
Safer, smarter information security, allowing you to better protect your organisation.
IT risk management eBook.
What IT risk is, why it matters, why it’s different from cyber risk, and why it’s not just a concern for the IT department.
Cyber risk management eBook.
How boards, executives and managers can meet their responsibilities to address growing and changing cyber threats.
Protecht ERM - end-to-end visibility and management of IT risks
Structured data
Centralised libraries and structured registers ensure efficient organisation across all IT risk management.
- Assets and asset risk ratings
- Compliance with multiple IT risk controls frameworks, controls assurance and statements of applicability
- IT security incidents and policies
- Your calendar of security activities, such as penetration testing
- Threat events
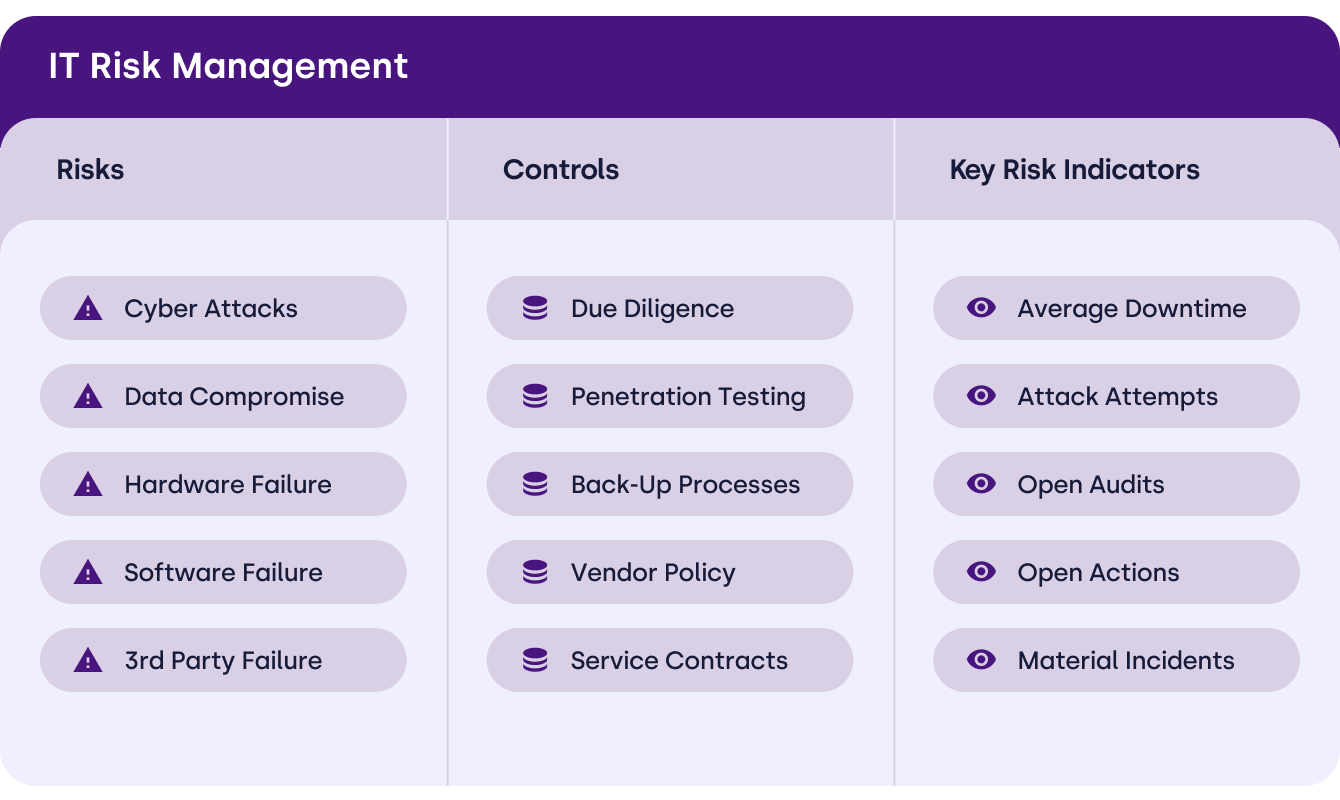
Risk visualisation and reports
Powerful visualisations and reports, making it easy to collaborate and communicate with all stakeholders from IT risk managers to senior management.
- Custom reports generated at the click of a button
- Risk bow tie tool to analyse root causes of IT risk events
- Dynamic, real-time risk profiles that visualise key information such as a risk’s related incidents, controls assurance, KRIs, attestations, issues and actions
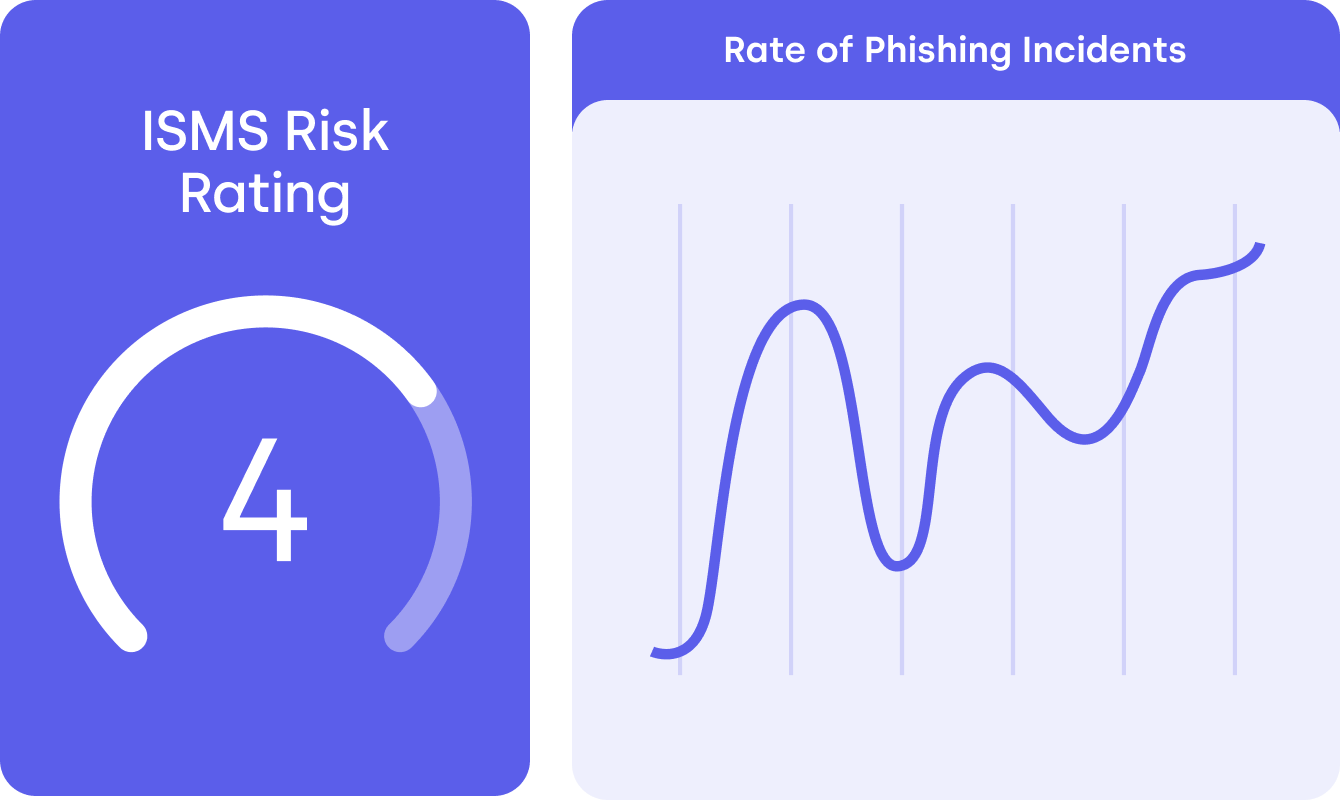
Regulatory obligations content and alerts
Preconfigured content - for a turnkey launch
Optimise your risk management at the click of a button. Set up and maintain your ERM system with Marketplace: preconfigured registers, dashboards and reports.
Popular register packages for IT risk management
ISMS - Security Calendar
Systematically capture and track important security events such as penetration test due dates, cryptographic key renewals, and audits. The ISMS Security Calendar register and dashboard allow you to:
-
Assign ownership and due dates to key events
-
Report on status of events and their completion
-
Provide a centralised repository of important security events
ISMS Control Library – ISO 27001
Provides a Control Library in line with the ISO/IEC 27001:2022 standard. These controls can be downloaded into the central library and tailored specifically to your organisation. The controls are also mapped to controls in SOC 2 Trust Services Criteria and NIST CSF, allowing customers to save time determining overlap in their implemented controls.
ISMS Control Library – NIST CSF
Provides a Control Library in line with the NIST CSF control framework. These controls can be downloaded into the central library and tailored specifically to your organisation. The controls are also mapped to controls in SOC 2 Trust Services Criteria and ISO 27001, allowing customers to save time determining overlap in their implemented controls.
ISMS Control Library – SOC2 POF & TSC
Provides a Control Library in line with the SOC 2 criteria. The SOC 2 POF (Point of Focus) control library has been designed by Protecht as suggested controls to comply with the SOC 2 TSC (Trust Services Criteria) requirements. These controls can be downloaded into the central library and tailored specifically to your organisation. The controls are also mapped to controls in NIST CSF and ISO 27001, allowing customers to save time determining overlap in their implemented controls.
ISMS Registers and Dashboards
Streamlines data capture and reporting to help organisations manage:
-
Controls, statements of applicability and assurance activities
-
Conducting and overseeing IT risk assessments
-
Asset and application risks
-
Cataloguing, reviewing and approving policies and documents
-
Minimising disruption from incidents
-
Visibility of ISMS actions
CISO Dashboard
Presents key information from the ISMS registers providing an overview of:
-
IT controls
-
IT risks
-
IT assets and their status
News and commentary
Related industries
Find out how Protecht’s industry expertise can help your IT risk management teams meet their business requirements across our key industry verticals:
-
Banking
Manage risk and compliance with a platform configured to empower financial services providers.
-
Insurance
Stay on top of regulatory requirements with real-time reporting that gives every user risk ownership.
-
Fintech
Manage risk and compliance with a platform designed for rapid growth in a rapidly changing environment.
-
Education
Manage risk with a platform configured to support staff, students and your business needs.
-
Government
Manage risk and compliance with a platform configured to meet the needs of government entities.
-
Industry
Manage your key risk needs – from compliance and vendor management through to health and safety.