All organizations rely on vendors. They provide us resources or capabilities that we don’t have, enable us to be competitive by leveraging their specific area of expertise, and allow organizations to focus on their core strengths (I’m not itching to generate my own electricity any time soon).
Those resources and capabilities allow organizations to deliver critical services to their customers – but it also means disruption to any one of those vendors may affect the resilience of your own operations.
In this blog we will cover how you can achieve visibility over all the links in your chain, identify the weak links that might undermine your operational resilience, and how you can forge stronger links. We will explore:
- How vendors link to the lifecycle of operational resilience
- Incorporating vendors into your operational resilience program
- Steps you can take to strengthen the chain
Subscribe to our Knowledge Hub to make sure you catch the rest of our Vendor Risk Management blog series:
The vendor link to operational resilience
Operational resilience is the ability to prevent, adapt, respond to, recover and learn from operational disruptions. Let’s break that down into three key phases of disruption, and how effective operational resilience and vendor risk management practices can help address them.
|
Phases of disruption |
Operational resilience and vendor risk management activities |
|
Pre-disruption |
Conducting vendor due diligence Implementing risk assessment and mitigation strategies Ongoing vendor controls assurance |
|
During disruption |
Agreed communication channels Coordinated incident response Practiced business continuity based on scenarios |
|
Post-disruption |
Conducting collaborative post-mortems Identify alternate vendor options and activate contingencies if needed Adapt business continuity plans, risk management strategies, and vendor monitoring |
While only one phase is pre-disruption, the only way these activities can be effective is have planned and tested them in advance of disruption. Before we explore some of those in more detail, we need to understand which vendors are important to consider.
A key component of an operational resilience program is having a comprehensive understanding of the resources needed to deliver critical services. This might include:
- Facilities
- Physical goods or assets
- Hardware
- Systems or software
- Information or data
- People
When you own these resources, you have much better line of sight into how vulnerable those resources are to disruption. That visibility can be murkier when provided by a vendor. Let’s work on that line of sight.
Identifying vendors linked to your critical services
You can follow these key steps to link vendors to your critical services:
- Identify the processes required to deliver your critical services
- Identify resources required for those processes, and separate them based on whether they are internal, or provided by a vendor
- Assess the criticality to the critical service if that resource were missing
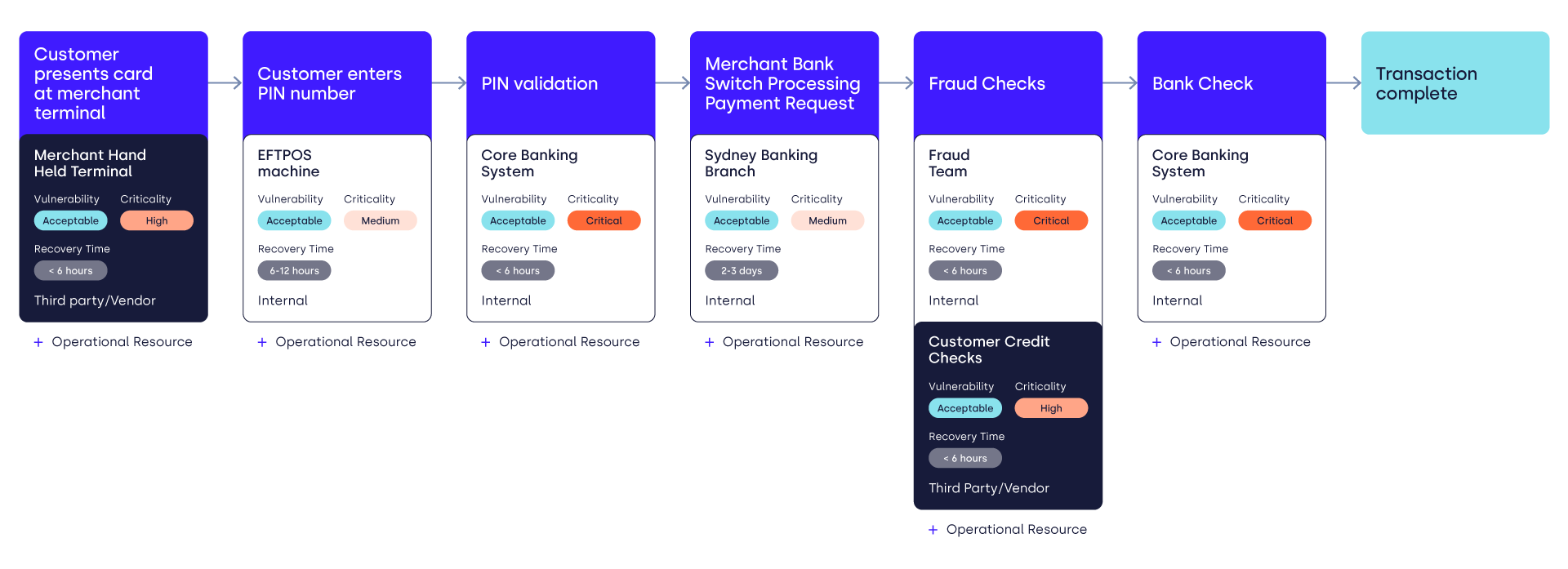
Process mapping can visualize where our critical vendors are in relation to delivery of our critical services. Below is an example of a simplified process map for customer payments at a merchant, highlighting the vendors involved in the process (click to open in a larger window):
Not only does this provide you with an end-to-end visualization for each of your critical services, it also enables you to collate a collective list of:
- Vendors who are directly involved in your critical processes
- The resources provided by those vendors
- The criticality of those resources
This information enables an integrated approach to operational resilience and vendor risk management. Vendors providing resources of the highest criticality should receive the most attention, but you should also consider vendors who provide several different types of resources across multiple critical services.
Pre-disruption
Prevention is better than cure. Effective upfront due diligence before you’ve even accepted and onboarded vendors sets clear expectations what you expect from them, and might even remove some vendors from the playing field that would otherwise undermine your operational resilience.
Use the criticality of the vendor and the resources they provide to influence your ongoing vendor monitoring. Identify the controls they have in place for risks that would affect the resources they provide, and agree on the frequency and level of detail required for controls assurance.
Consider contractual clauses that outline your expectations for this assurance, and any other operational resilience activities you expect them to participate in.
During disruption
While prevention is better than cure, a complete operational resilience program needs to consider how you respond and adapt, assuming that disruption has already occurred.
The plausible scenarios you develop might include two ways that vendors could fail – either a particular resource, or all of their resources if they provide multiple. A plausible but extreme scenario might include a vendor who suffers a cyber intrusion, where they subsequently disable all their digital services as a precautionary measure.
While you could choose to assess scenarios as internal desktop exercises, the best approach is to actively involve and collaborate with the vendor. This enables:
- Clarity on how disruptive incidents are initially communicated – which tools are used, and any escalation pathways
- Greater understanding by the vendor of their importance to your critical services, which may prompt additional proactive assurance from the vendor
- Collaboration and joint discovery of potential causes of disruption, enabling the implementation of additional control measures
- Improvement to business continuity or recovery plans, particularly if the vendor identifies other resources or capabilities they can offer during disruption
After exploring these plausible scenarios, you need to develop a plan to respond, and test them. This allows you to adapt strategies that might look good on paper, but may not work in all scenarios. These tests provide greater assurance that the vendor will respond in the way you expect – particularly that their own response and recovery times align with your own expectations.
Post-disruption
After initial recovery is in place and services are returning to normal, there is an opportunity to learn and adapt. The most important step is a post-mortem with the vendor. This helps to:
- Identify the specific causes of the disruption
- Assess the effectiveness of the response
- Verify whether any controls or assurance processes failed
- Clarify whether roles and responsibilities were understood
- Assess whether any business continuity or response plans were effective
This analysis can then drive the following improvements:
- Updates to business continuity plans
- Implementing additional controls (either internal or by the vendor) or key risk indicators
- Changes to the frequency or granularity of ongoing monitoring over the vendor
If necessary, you may need to enforce contract clauses with the vendor, or end or change the relationship based on the information learned in the post-mortem.
Conclusions and next steps
There are very few critical services that organizations provide which don’t rely on vendors. Don’t let them be the weak link in your operational resilience. Key take-aways include:
- Document the vendors involved when you map out your critical services
- Ensure sufficient due diligence and monitoring of vendors who provide critical resources
- Treat vendors as part of your extended enterprise; take a collaborative approach to include critical vendors in your operational resilience processes, such as incident management
- Support these processes with systems and tools that enable a single source of truth and provide an integrated view of vendors, risks, and operational resilience
If you want to know more about your vendor risk, download our Vendor Risk Management eBook for a detailed step-by-step guide of to build an effective vendor risk management program.
Subscribe to our Knowledge Hub to make sure you catch the rest of our Vendor Risk Management blog series: